
The era of Cyber Security is over!
Cyber Warfare Threatens Every Organization
-
 Unknown-Unknowns that keep the CISOs awake at night
Unknown-Unknowns that keep the CISOs awake at night
-
Most AI and Machine Learning techniques learn pre-determined rules required to detect attacks, where models are built to detect features from samples of historical attacks. So how do you discover and detect unknown attacks whose signatures are also unknown?
Nodal takes another approach. We analyze the Attack Path from historical communications that occurred from hotspots of Signals within the victim's network at a large scale, and identify the potential entry points for an attacker. Learn more about Attack Path Analysis:
-
 Breakouts Happen Fast, Defense Must Be Faster
Breakouts Happen Fast, Defense Must Be Faster
-
Every second an adversary lingers brings them closer to a breakout — and compromises more systems.
95% of global enterprises can’t meet the 1/10/60 rule. Minutes are too slow. Effective security operates in seconds..
For an attack to suceed, an adversary needs to gather intelligence about their victim and remain elusive
But through the fog of cyberwar... Nodal Sees It All
Nodal detects & disrupts an adversary from gaining that intelligence so an attack does not materialize
Introducing the
Nodal CyberBrain
We didnt invent Network Detection & Response. But we've perfected it!
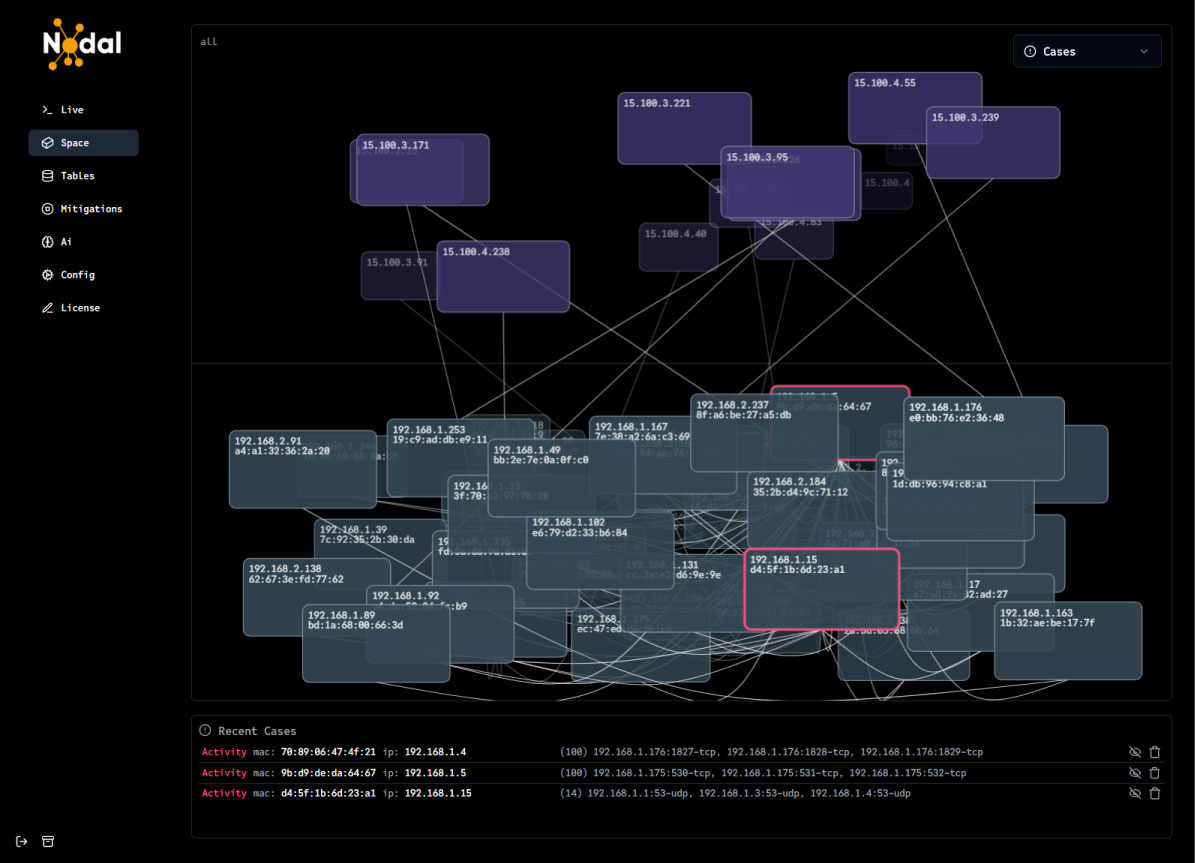
Instantly pinpoint attackers and expose the chain of compromised devices and services
Nodal’s CyberBrain AI accurately distinguishes between legitimate traffic and malicious communications in seconds, and automatically disrupts adversaries.
How long is acceptable… while dwellers and malware are already inside?
Threats Don’t Wait. Neither should you.
While other products focus on mapping techniques and tactics, with detection times measured in minutes at best, threats in your network are already unfolding. Every minute spent analyzing and managing alerts gives attackers more time to move, hide and strike. Nodal detects adversaries the moment they begin communicating inside your network, identifying their path, breaking their persistence, and blocking off any intelligence gathering. In seconds, not minutes!
How Nodal's CyberBrain is different
Instantly Pinpoint Compromised Devices
No more guessing where attackers dwell – Identify the breach in the network the moment it happens.
Maps multi-nodes communication relays
Tracks malicious communications that relay between multiple internal and external devices, exposing the most complex and stealth attack paths. Security professionals can now pinpoint compromised devices and remediate without having to pull the plug on entire operations.
Smart, Aggressive Mitigations
Smart mitigation responses that immediately stop adversaries in their tracks both North-South, and East-West, never letting your privacy leave the network.
Catching the Unknown-Unknowns within the network
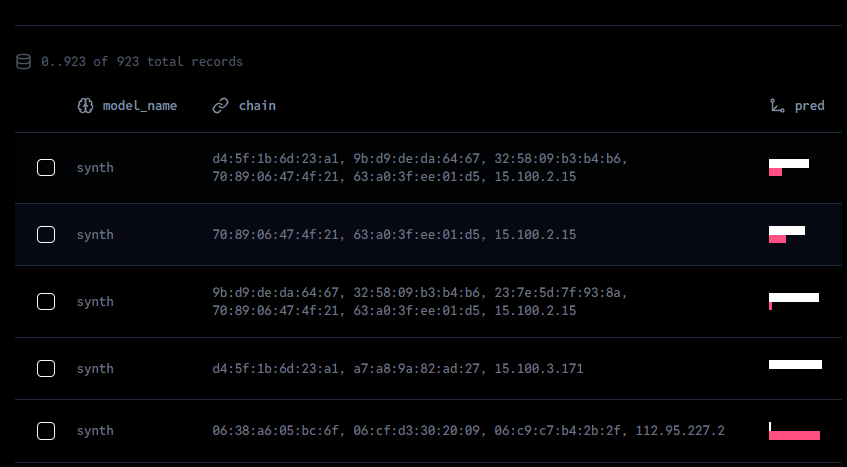
Instead of building specific detection models that will fail against unknowns, the CyberBrain inferences against any network and service communications indiscriminately from a hotspot of Signals and estimates the most likely path of attackers.

Seamlessly integrates with your existing tools
An easy to use Nodal SDK and API, connects with a few lines of code to your favorite SIEM, SOAR, Firewalls, Zero-trust and micro-segmentation tools.
import asyncio
from nodal_sdk import Mitigator
from nodal_sdk.types import MitigationRequest, MitigationResponse
async def start():
mitigator = Mitigator(name= "MyMitigator", port=9999)
await mitigator.register(ip=mit_ip, handshake_uri=ghost_uri, token=ghost_token)
while True:
if cmd == "mitigation":
response = handle_request(data)
if response:
mitigator.send("mitigation", response)
def handle_request(req: MitigationRequest) -> MitigationResponse | None:
''' Your code goes here '''
Edge Native, Ready to Hunt on Day 1.
Nodal CyberBrain is a Software-Hardware solution that's easy to install. A simple Plug-and-Play machine, no baselining required, no rip-and-replace, and it is ready to hunt on day 1.
Paired with remote probes, the CyberBrain scales with the size of your network, monitoring any environment on-premise, cloud, IT/OT, and across the country or world.

Nodal CyberBrain is deployed in three form factors: An easy to carry Mini-PC; as a Rackmount Server; or as a Virtual Machine. Plug the CyberBrain to a mirror port on your network access point, then power it on, and you are ready to go. It is that easy!
A technology breakthrough in Artificial Intelligence technologies with stunning compute cost to performance ratio
And yet, CyberBrain has both precision and speed
- Packets Per Seconds (PPS) traffic
- 4,000,000+
- Networks monitored per CyberBrain
- Hundreds
- To hunt dwellers across the network
- 1.4 seconds
- Fewer alerts and SOC fatigue
- 99%
Industry Recognition
" The CyberBrain gives me actionable intelligence visually at the click of a mouse. It is rapidly becoming my most important threat hunt tool. It is one of the most innovative cyber security tools I have seen in years.... maybe even decades! "
" At JSI Telecom US, we provide critical information needs to governments around the world. The Nodal Cyber brain is an integral part of our information security defense in depth strategy. We us it in multiple places within our infrastructure to detect against malicious intrusions and accidental disclosures. It provides us with certainty we see clearly any anomalous activity in our environment. Our company and customers can rest assured we see and eliminate threats in near real time. "
" At Essential health we protect the health care of numerous high value (wealth) individuals and organizations. We are meticulous about our cyber defense strategy and defense in depth of our information technology environments. We view and use the Nodal Technologies Cyber brain as the last line of defense in our arsenal. It catches that which others do not. Including that which our employees miss or in fact cause. It is our secret weapon against cyber adversaries. "